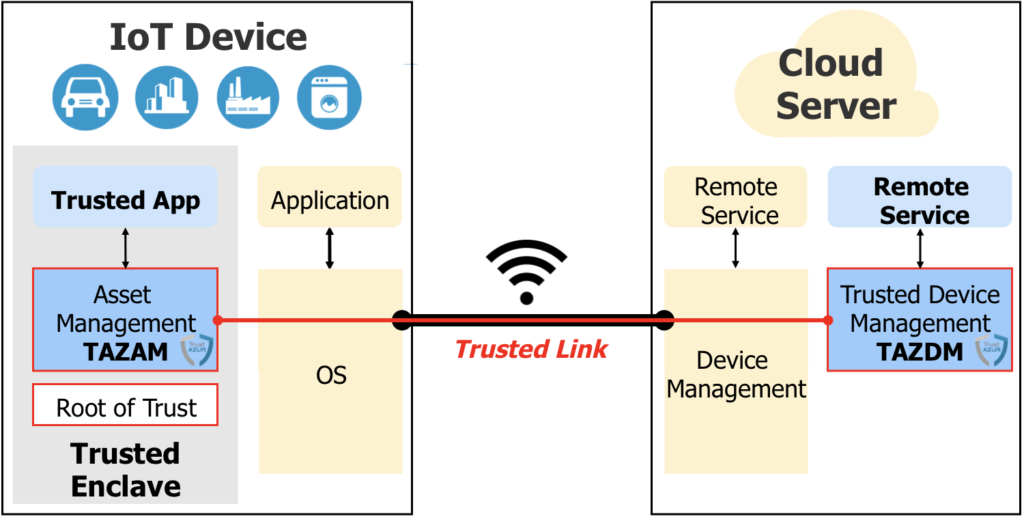
TAZAM is the TrustAZUR Asset Management solution to provision, store and manage assets to secure communication between Trusted Applications and Remote Services in the Cloud
- Trusted Applications
- OS Applications
- Cloud Remote Services
- Trusted OS-less: execute on Bare Metal HW Enclave
- Trusted OS-based: execute as an application in an OS Environment (OP-TEE, Arm Trusted Firmware-M)
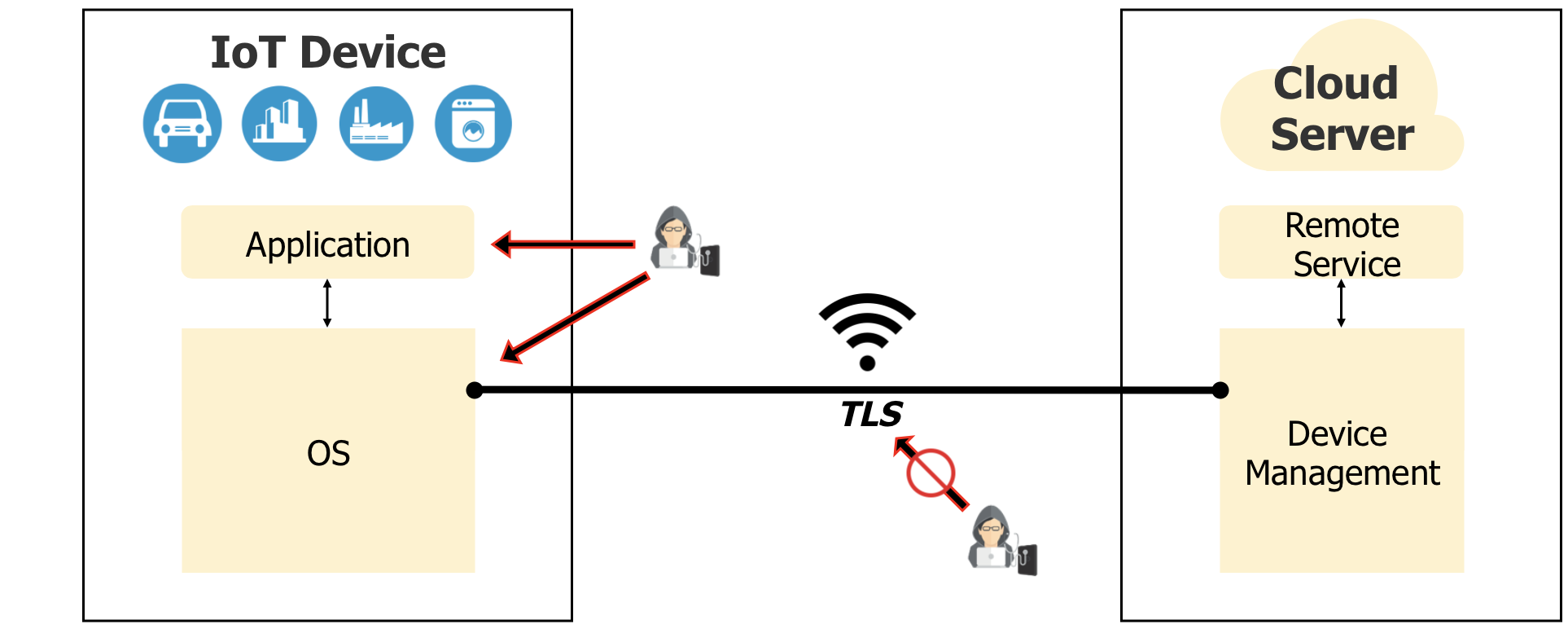
In IoT space, communication protection is not just about protecting against eavesdropping of data in transit. IoT Devices, which are open devices, can be hacked by installation or injection of malicious data or software at any given time through wireless or wired interfaces.
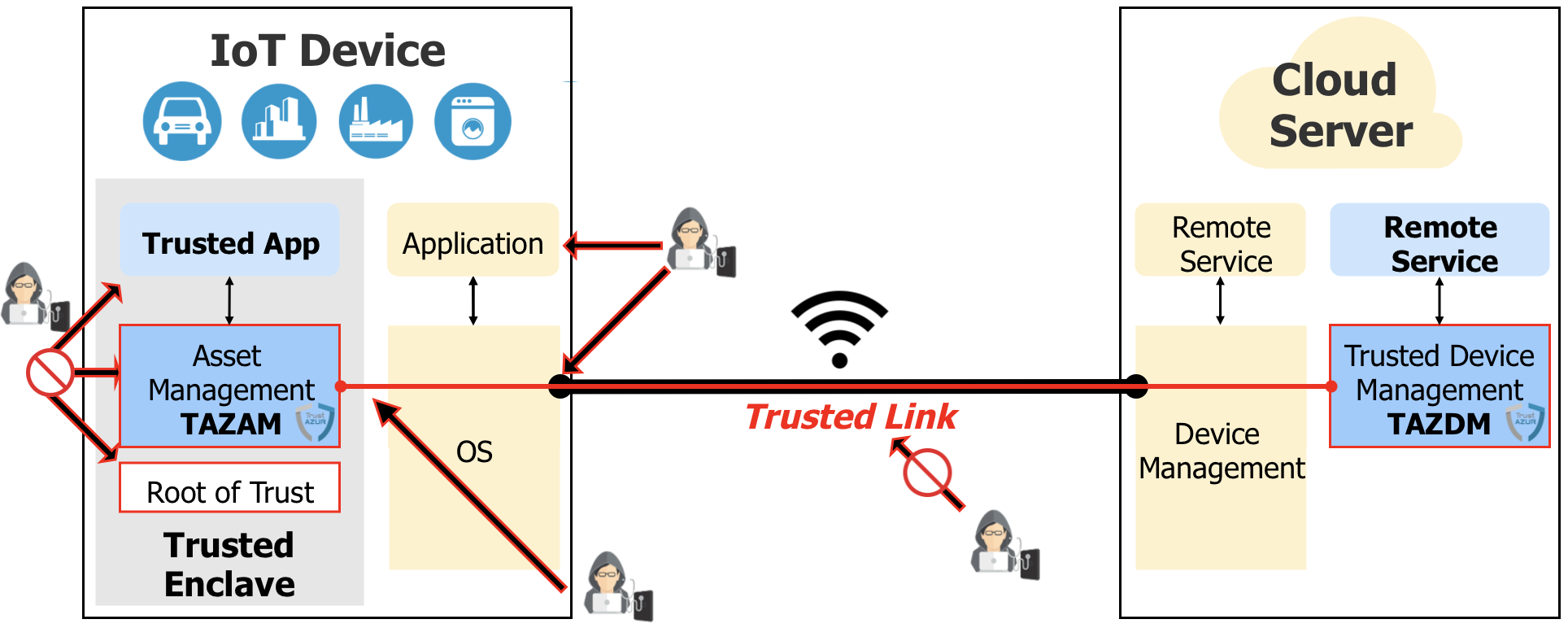
Because device interfaces are controlled and managed by Non-Trusted software, it is critical that sensitive software and assets stored and processed on the device are protected within a Trusted Enclave, and are safeguarded when remotely accessed from outside of the Trusted Enclave.
The level of protection of software and assets on a given platform depends on the capabilities of fundamental security technologies present on the he platform: Root of Trust, Trusted Enclave, Asset Management.
Protection on today’s IoT Devices
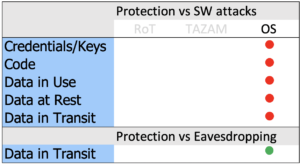
In the absence of all fundamental security technologies on such kind of device, no protection against software attacks can be implemented. Assets, data and software are fully exposed to attacks through the open device OS ( ).
Protection of data in transit can be achieved by using secure protocols, like TLS, which encrypt data before sending it out of the device ( ).
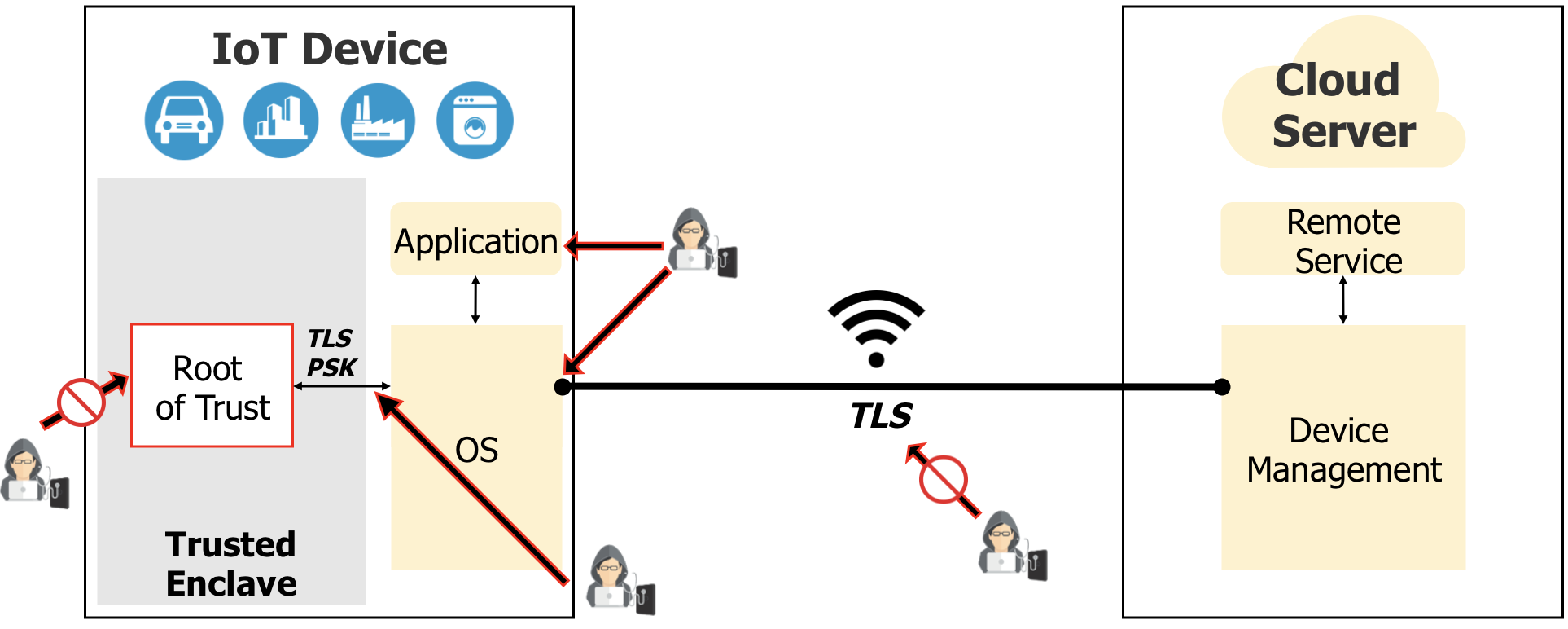
Protection of IoT Devices implementing a Root of Trust
In this case, initial assets and RoT software are protected in the RoT component ( ).
Mitigation mechanisms can be possibly introduced against non-secure software injection and device cloning/impersonation ( ).
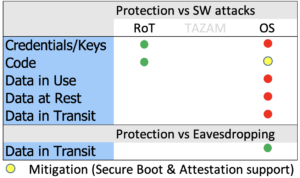
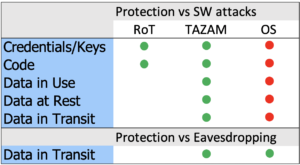
Protection of IoT Devices with an RoT and TAZAM
In this case, protection against device cloning/impersonation is achieved, as well as protection of data processed in the Trusted Enclave and sent to Remote Services by the means of a TAZAM Trusted Link ( ).
``I want to protect my device versus impersonation and cloning``
- TAZAM installs a Trusted Device Identity which ensures that it is an OEM or Service Provider approved device
- Such Identity is used to remotely authenticate the device
``I want to protect my software running on my platform``
- TAZAM authenticates SW at Boot Time and Run Time (Attestation)
- TAZAM supports FW Update Management
``I want to protect my credentials``
- TAZAM stores sensitive data into its asset storage and provides access control capabilities to this data
- TAZAM leverages Trusted Domains to isolate Asset Storage areas owned by different Service Providers
``I want to securely communicate with a remote server``
- TAZAM establishes a Secure Connection (Trusted Link) with Mutual Authentication to a remote server on top of an existing logical connection (MQTT, TCP/IP)
``I want to execute security services in the device from a remote server``
- Client Applications easily request Security-related Services execution to TAZAM via commands interface
``I want to provision assets into the platform``
- Cloud Remote Services (leveraging TAZDM reference implementation) can provision assets into TAZAM which can be shared with Trusted Applications
``I want to securely send messages between device and server``
- TAZAM includes a Trusted Messaging component to exchange messages between Trusted Applications and Remote Services
``Is TAZAM replacing Arm Trusted Firmware-M or Linaro OP-TEE?``
- TAZAM is extending Arm TF-M and OP-TEE capabilities by providing a secure connection to Remote Services
- TAZAM can work bare metal if no underlying Trusted OS runs in the Trusted Enclave
- TAZAM can also be executed as a Secure Application if the platform includes a Trusted OS within the Trusted Enclave
TAZAM-C: Microcontroller Bare Metal
Cypress PSoC 6 (Arm Cortex M0+) / Amazon FreeRTOS NXP LPC55S69 (Arm Cortex M33 -v8M) / AmazonFreeRTOS
TAZAM-M: Arm TF-M Partition
Arm Musca Board (V8-M), Arm Trusted Firmware-M, Arm Mbed OS
TAZAM-T: TEE Trusted Service
Raspberry Pi, Linaro OP-TEE, Linux / Android
AWS IoT
MQTT
IBM Cloud
MQTT